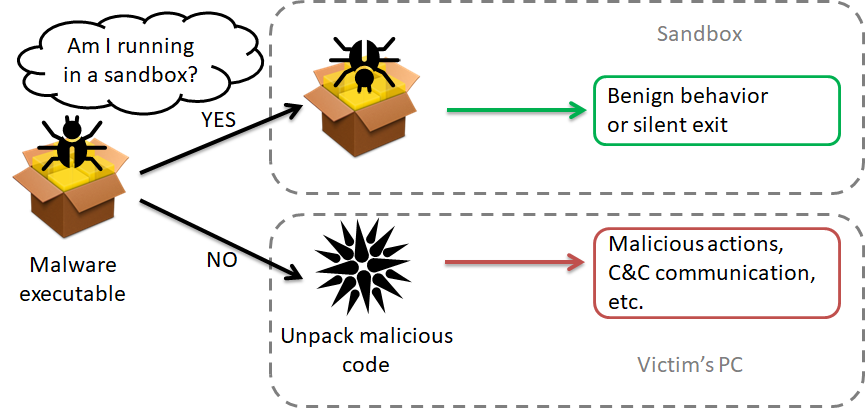
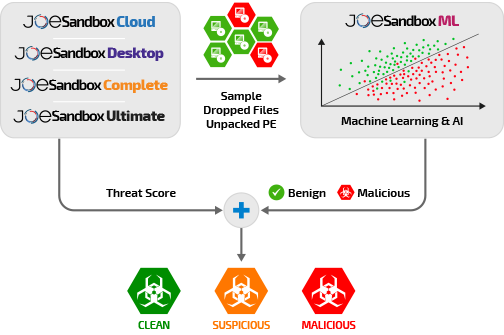
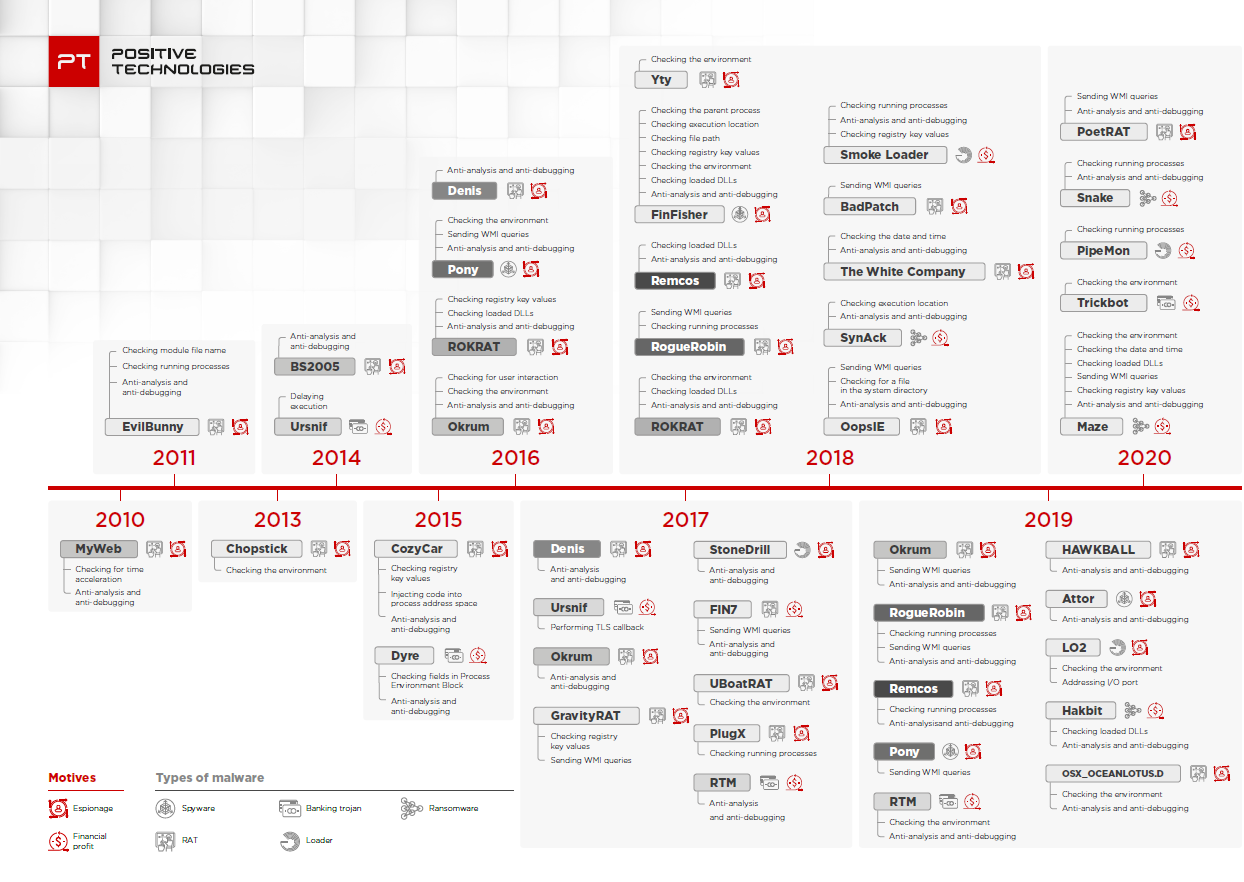
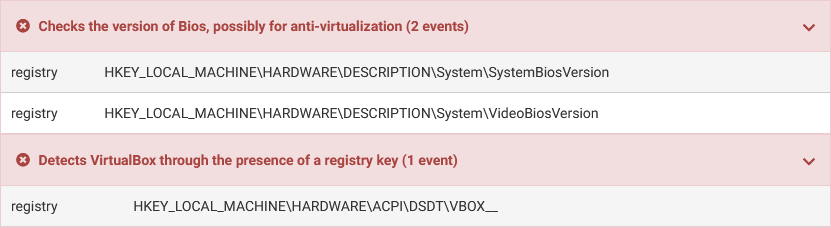
Bypassing modern sandbox technologies An experiment on sandbox evasion techniques | Semantic Scholar
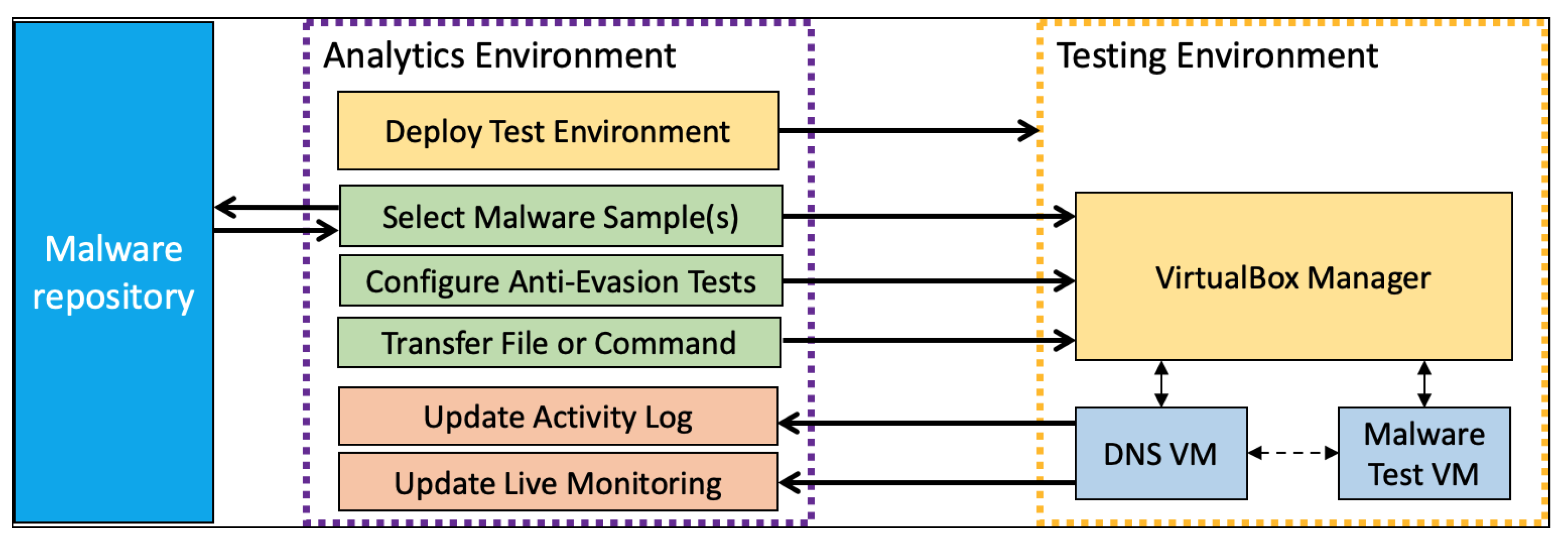
JCP | Free Full-Text | Investigating Anti-Evasion Malware Triggers Using Automated Sandbox Reconfiguration Techniques | HTML

Defeating Sandbox Evasion: How to Increase Successful Emulation Rate in Your Virtualized Environment - 2017 ShmooCon Proceedings